7 Types of Application Security Testing Tools You Must Know About
As a developer or security professional, you’re well aware of the critical importance of application security in today’s digital landscape. With cyber threats evolving at an alarming rate, it’s essential to fortify your applications against potential vulnerabilities.
Application security testing tools are your first line of defense, offering comprehensive protection for your software throughout its lifecycle. But with numerous options available, how do you choose the right tools for your needs? In this article, we’ll explore seven indispensable types of application security testing tools that you must know about to ensure robust protection for your applications and safeguard your organization’s digital assets.
What is Application Security Testing?
Application Security Testing (AST) is a crucial process in software development that identifies vulnerabilities, weaknesses, and potential security threats in applications. This comprehensive approach involves analyzing both the application’s source code and its runtime behavior to uncover potential security flaws.
Application security testing encompasses various techniques, including static analysis, dynamic testing, and interactive application security testing. By implementing AST, organizations can proactively detect and address security issues early in the development lifecycle, reducing the risk of data breaches and cyber attacks. This process not only enhances the overall security posture of applications but also helps ensure compliance with industry standards and regulations.
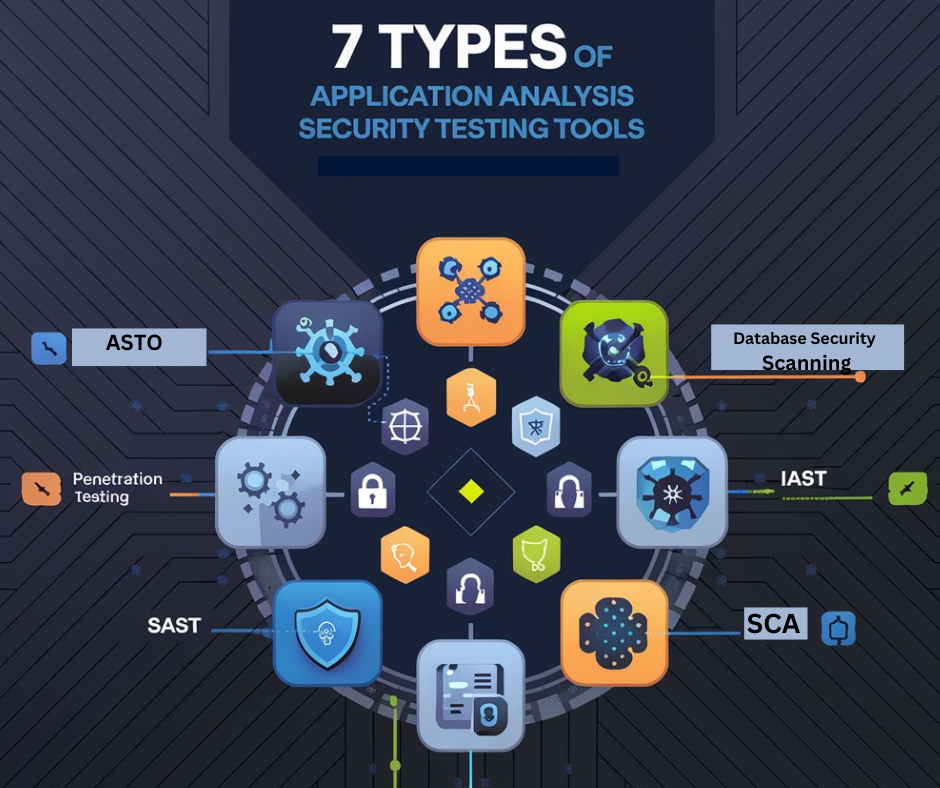
7 Types of Application Security Testing Tools

In today’s digital landscape, Application Security Testing (AST) is crucial for safeguarding software from potential vulnerabilities and attacks. There are seven primary types of AST tools that developers and security professionals must be familiar with to ensure comprehensive protection. These tools range from static analysis that examines source code without execution, to dynamic testing that evaluates running applications.
Understanding these diverse tools is essential for implementing a robust security strategy and maintaining the integrity of your applications in an ever-evolving threat landscape.
- Static Application Security Testing (SAST)
Static Application Security Testing (SAST) is a crucial tool in your application security arsenal. This white-box testing method analyzes source code, bytecode, or binary files to identify vulnerabilities and weaknesses before the application is deployed. Static application security testing tools scan the entire codebase, detecting potential security flaws such as SQL injection, cross-site scripting, and buffer overflows.
Key Benefits of Static Application Security Testing
SAST offers several advantages:
- Early detection of vulnerabilities
- Cost-effective bug fixing
- Compliance with industry standards
By integrating SAST into your development lifecycle, you can significantly reduce security risks and improve overall code quality. However, it’s important to note that SAST should be used in conjunction with other testing methods for comprehensive application security.
- Dynamic Application Security Testing (DAST)
Dynamic Application Security Testing (DAST) is a crucial component of application security that analyzes running applications to identify vulnerabilities. Unlike static testing, DAST simulates real-world attacks on a live system, providing insights into how an application behaves under actual threat conditions.
Dynamic Application Security Testing tools scan web applications, APIs, and services from the outside, mimicking malicious users. They probe for security weaknesses such as SQL injection, cross-site scripting (XSS), and authentication flaws. This “black box” approach allows DAST to detect issues that might be missed by code analysis alone.
Benefits and Limitations of Dynamic Application Security Testing
Dynamic Application Security Testing excels at finding runtime and environment-related vulnerabilities. However, it may struggle with complex authentication mechanisms and can be time-consuming for large applications. Despite these challenges, DAST remains an essential tool in comprehensive application security testing strategies.
- Interactive Application Security Testing (IAST) & Hybrid Tools
Interactive Application Security Testing (IAST) combines the strengths of static and dynamic testing methodologies. This innovative approach monitors application behavior in real-time during runtime, providing comprehensive insights into potential vulnerabilities. Interactive Application Security Testing tools integrate seamlessly with existing development processes, offering continuous security feedback without disrupting workflows.
Hybrid tools take this concept further by blending multiple testing techniques. These versatile solutions may incorporate elements of SAST, DAST, and IAST, along with other security measures like penetration testing or threat modeling. By leveraging diverse methodologies, hybrid tools offer a more holistic view of an application’s security posture, helping organizations identify and address a wider range of potential threats throughout the software development lifecycle.
- Database Security Scanning
Database security scanning is a critical component of application security testing. This process involves thoroughly examining your database systems for vulnerabilities, misconfigurations, and potential access points that malicious actors could exploit. By utilizing specialized tools, you can identify weak points in your database architecture, such as outdated software versions, insecure default settings, or improperly configured user permissions.
These scans also help detect SQL injection vulnerabilities, one of the most common and dangerous threats to database security. Regular database security scanning allows you to maintain a robust security posture, ensuring the confidentiality, integrity, and availability of your sensitive data. Implementing this practice as part of your overall application security strategy is essential for protecting your organization’s critical information assets.
- Mobile Application Security Testing (MAST)
Mobile Application Security Testing (MAST) is a crucial process for ensuring the safety and integrity of mobile apps. This specialized form of application security testing focuses on identifying vulnerabilities specific to mobile platforms. Mobile Application Security Testing examines both the client-side application and server-side components, assessing potential risks in areas such as data storage, communication protocols, and authentication mechanisms.
Key Components of Mobile Application Security Testing
- Static Analysis: Reviewing source code for security flaws
- Dynamic Analysis: Testing the app in a running state
- Penetration Testing: Simulating real-world attacks
MAST tools help developers identify and address security issues unique to mobile environments, such as insecure data storage, weak encryption, and improper platform usage. By implementing MAST, organizations can significantly enhance the security posture of their mobile applications, protecting both user data and company assets.
- Origin Analysis/Software Composition Analysis (SCA)
Origin Analysis, also known as Software Composition Analysis (SCA), is a crucial application security testing tool that examines the components of your software. This process identifies and tracks third-party and open-source components within your application, helping you manage potential vulnerabilities and licensing issues.
SCA tools scan your codebase, comparing it against databases of known vulnerabilities and license information. They provide detailed reports on the origin, version, and security status of each component. This allows development teams to quickly identify and address any security risks or compliance issues before they become problematic.
By implementing SCA, organizations can maintain better control over their software supply chain, ensure compliance with licensing requirements, and proactively mitigate security threats associated with third-party components.
- Application Security Testing Orchestration (ASTO)
Application Security Testing Orchestration (ASTO) is a sophisticated approach that streamlines and automates the integration of various security testing tools throughout the software development lifecycle. This methodology enhances efficiency by coordinating multiple testing processes, from static analysis to dynamic testing, and consolidating results into a unified dashboard.
ASTO platforms typically offer features such as centralized management of security tools, automated test scheduling, and comprehensive reporting capabilities. By implementing ASTO, organizations can significantly reduce the time and resources required for security testing while improving overall application security posture. This approach is particularly valuable in DevSecOps environments, where rapid and continuous security assessment is crucial for maintaining a robust defense against evolving threats.
How Often Should Application Security Testing Be Performed?
It depends on factors like the risk level of the application, development cycle time, and resources. In general:
- During development: As often as new code is committed – ideally as a “shift left” process through DevSecOps.
- Before release: At minimum, before any major release to production to catch any late-stage issues.
- Post-release: On a regular cadence (monthly, quarterly, etc.) to identify new vulnerabilities over time.
- Ad-hoc: As needed in response to new threats or security incidents.
The goal should be to integrate security testing into the SDLC for a proactive and continuous approach.
Choosing the Right Application Security Testing Approach for Your Needs
Selecting the appropriate application security testing approach is crucial for effective vulnerability detection. Consider your organization’s specific requirements, development lifecycle, and resource constraints. Automated tools offer speed and scalability, ideal for large codebases or frequent releases. However, manual testing provides deeper insights and context-aware analysis, essential for complex applications or high-risk areas.
A hybrid approach often yields the best results, combining automated scans with targeted manual testing. Prioritize critical assets and high-risk functionalities for more intensive scrutiny. Additionally, consider integrating security testing throughout the development process, rather than relying solely on pre-release assessments. This shift-left approach helps catch vulnerabilities earlier, reducing remediation costs and improving overall security posture.
10 Best Change Management Software Tools in 2024http://hitechhive.com/10-best-change-management-software-tools-in-2024/
Conclusion
As you implement application security testing into your development process, consider leveraging a combination of these tool types for comprehensive protection. Static, dynamic, and interactive testing provide complementary coverage, while mobile and API-specific tools address unique vulnerabilities. Penetration testing and fuzzing round out a robust security strategy.
Remember, no single tool can catch every potential flaw. By employing multiple testing methods throughout the software lifecycle, you’ll dramatically reduce risk and strengthen your overall security posture. Stay vigilant, keep tools updated, and make security testing an ongoing priority. Your users and your organization will thank you for the enhanced protection against ever-evolving cyber threats.



