What is Email Archiving? | How to and Why You Should
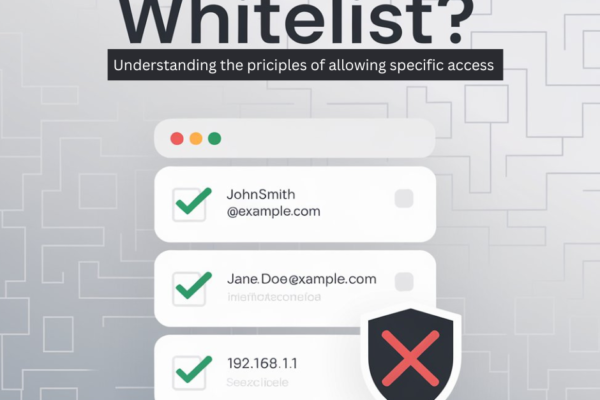
Email has become the lifeblood of modern business communication, but managing the ever-growing volume of messages can be overwhelming. Email archiving is a powerful solution that helps you efficiently store, organize, and retrieve your organization’s email correspondence. As regulatory compliance and data retention requirements become increasingly stringent, implementing a robust email archiving strategy is no…